YAAC has the capability to verify if a message was actually sent by the station that claims to have sent it, while still complying with national laws requiring amateur radio traffic to be sent "in the clear" (unencrypted). Using standard timestamped HMAC (Hashed Message Authentication Code) algorithms, YAAC can append a cryptographic signature to an APRS message that can only be confirmed by other stations with which a common encryption key has been shared (presumably through some secure means, not over APRS). This can be used for any purpose where the recipient needs to confirm that the claimed transmitting station actually did send the message, such as telecommand, and that the message is not being replayed at a later time by some other station.
If the user accesses the keystore to see and edit what keys are available (from the View menu), a table of keys currently stored in the keystore will be displayed.
The key table will list the arbitrary name associated with each key, what type of key (secret symmetrical key or public/private asymmetrical key), and which other stations (callsign-SSID combinations) this key has been shared with. Buttons are provided to:
When the user sends a message to another station (using any of the mechanisms for doing so in the GUI), YAAC will check if the recipient station has been associated with local security keys. If so, YAAC will ask if the message should be signed, and (if more than one local key is associated with the remote station) which key should be used. Note that only symmetrical (secret) keys can be used for message signing; private/public key pairs create a signature too long to use in APRS messages. If you choose to sign the message, a signature will be generated using the current time (in 1-minute resolution, 32-bit binary high-byte-first minutes since the Unix time epoch of midnight, January 1st, 1970 UTC), the recipient's callsign-SSID (as a variable-length ASCII string, not AX.25 bit-shifted encoding), and the text body of the message, and appended to the sent message (before any acknowledgment sequence number), as the literal text "\S" followed by a base-85 encoding of the 16-byte MD5 hash (expanding to 20 non-blank ASCII characters). The 1-minute-resolution time protects against replay attacks by invalidating the signature should the message be received more than one minute after it was originally transmitted.
If the user receives a signed message from another station, and the other station is associated with locally-known secret keys, YAAC will attempt to validate the signature. If the signature is successfully validated (either against the current time or the previous minute's time), the message will be displayed in green text (rather than the usual black text) in message display windows. If the signature fails validation, the message will be displayed in magenta (purplish-red), so you know the message is not valid (corrupt or invalid format APRS messages are also displayed in magenta). The message data structure is marked internally with flags that can be tested programmatically by YAAC plugin extensions.
Note that this message authentication mechanism is based on research originally reported by Bryan Hoyer KG6GEU in a presentation to the NW Digital Radio group on 2013-Mar-31, available at https://microhams.blob.core.windows.net/content/2015/05/KG6GEU_Authentication.pdf.
Note that authentication using this mechanism requires that both the sender and receiver stations have their system time synchronized within one minute of each other, so that the correct timestamp will be used to validate the signature. Since most APRS stations are either using a GPS receiver (which provides time with fractional second accuracy) or are connected to the Internet (and thereby have access to Network Time Protocol servers to keep their clock synchronized), maintaining clock accuracy should not be an issue. However, if you constantly receive signature failures, check your system time to ensure it is accurate, and validate that you can get a message to the other station (or vice versa) in under a minute.
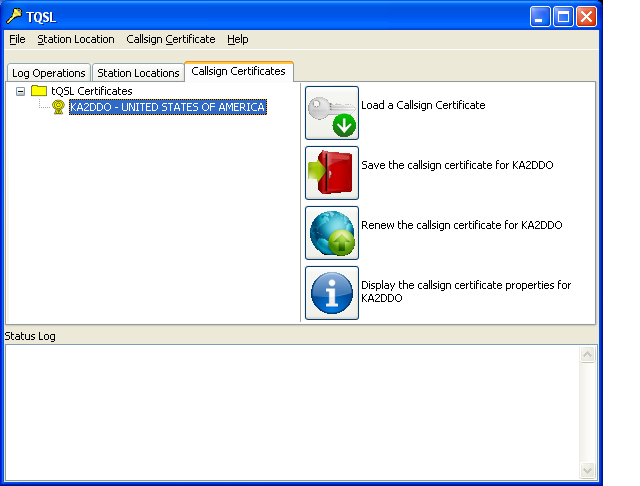
Private/public key pairs can be used as an alternative to the insecure APRS-IS passcode to authenticate YAAC to the APRS-IS Tier 2 backbone, using the SSL-APRS-IS port type. Only key pairs used for the ARRL Logbook of the World and certified by the ARRL's Certificate Authority are acceptable.
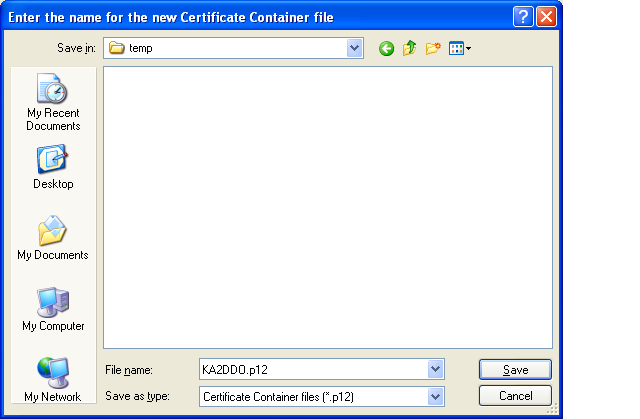
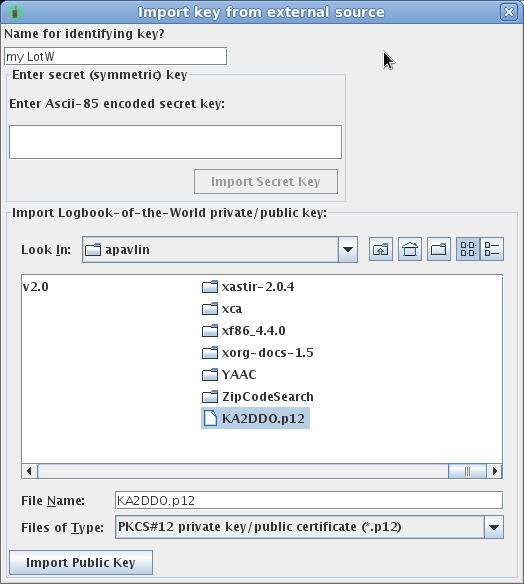
To import a private/public key pair, follow the procedures documented for the ARRL's TQSL or trustedQsl programs (depending on your operating system) to register yourself with the ARRL's Logbook of the World (LotW). Then export your private/public key pair as a PKCS#12 keystore file, making sure you specify a password to protect the contents of the keystore: